According to the US Department of Homeland Security, the manufacturing industry is the second most targeted industry when you look at the number of reported cyber attacks. Why? Cyber criminals view small and medium-sized manufacturers as prime targets precisely because many of these companies do not have adequate preventative measures in place.
With more than 289,000 small manufacturers in the United States, small manufacturers are a vital part of our nation’s economic and cyber infrastructure. For most small manufacturers, the security of information, systems, and networks is not the highest priority, but a cybersecurity incident can be detrimental to the business, customers, or suppliers. It’s important that manufacturers understand and manage the risk and establish a cybersecurity protocol to protect critical assets.
Five Steps to Reduce Cyber Risks
This resource is for small manufacturers to quickly and cost-effectively address cybersecurity threats. These simple, low-cost steps are based on the official NIST guidance from the Cybersecurity Framework and have been tailored to meet the needs of small companies so they can identify, assess and manage cybersecurity risks.
The NIST Cybersecurity Framework
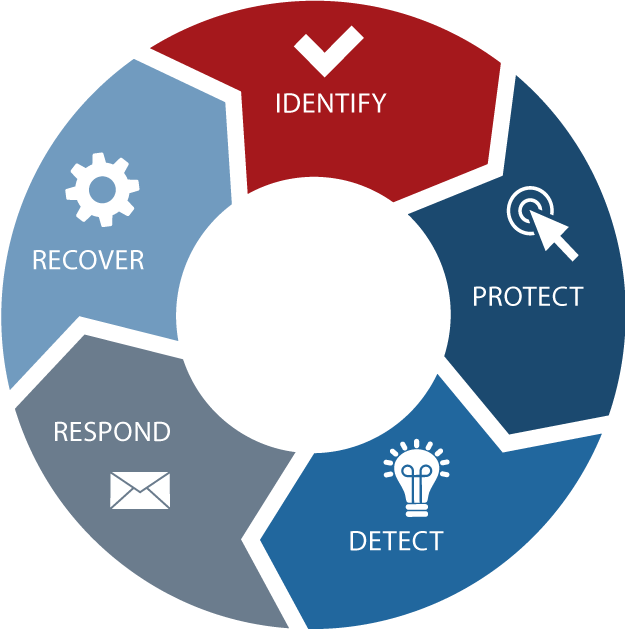
IDENTIFY
Develop an organizational understanding to manage cybersecurity risk to systems, people, assets, data, and capabilities.
PROTECT:
Develop and implement appropriate safeguards to ensure delivery of critical services
- Identify and control who has access to business information
- Conduct background checks
- Require individual user accounts for each employee
- Create policies and procedures for cybersecurity
DETECT:
Develop and implement appropriate activities to identify the occurrence of a cybersecurity event.
- Train employees and limit employee access to data
- Install surge protectors and uninterruptible power supplies
- Patch operating systems and applications routinely
- Install and activate firewalls on all business networks
- Set up web and email filters
- Use encryption for sensitive information
- Dispose of old computers and media safely
RESPOND:
Develop and implement appropriate activities to take action regarding a detected cybersecurity incident.
- Develop and maintain a plan for disasters and cyber incidents
- Notify your customers and the authorities
RECOVER:
Develop and implement appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity incident.
- Make full backups of important business data and information
- Schedule incremental backups
- Improve processes, procedures, and technologies